OAuth в мобильных приложениях

Creating a Secure Login on Android Using Google OAuthSee more
OAuth 2.0 Auth Code Injection Attack in ActionSee more

How to make your Mobile App Secure? | Mobile App Security Best Practices | Build a Secure Mobile AppSee more

Аутентификация и авторизация в веб-приложенияхSee more

How to Hack OAuthSee more

OAuthSee more

What's the difference between Confidential and Public clients? - OAuth in Five MinutesSee more

OAuth: Past, Present, and Future | Developer Day 2021See more

Everything You Ever Wanted to Know About OAuth and OIDCSee more
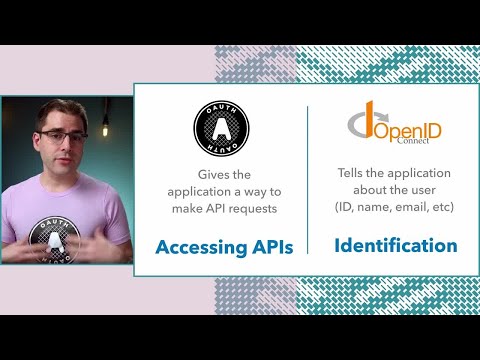
What is OAuth and why does it matter? - OAuth in Five MinutesSee more

How Google is using OAuth - Part 1: Understanding OAuth at GoogleSee more

An Illustrated Guide to OAuth and OpenID ConnectSee more

1000 Ways to Die in Mobile OauthSee more

OAuth: When Things Go WrongSee more

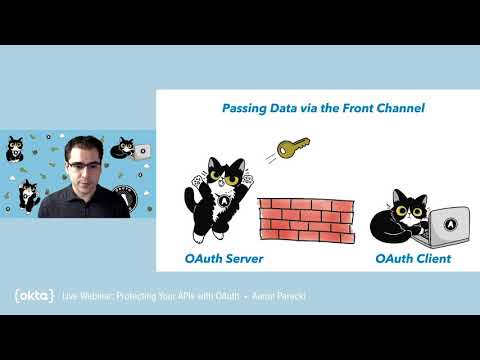
Protecting Your APIs with OAuthSee more
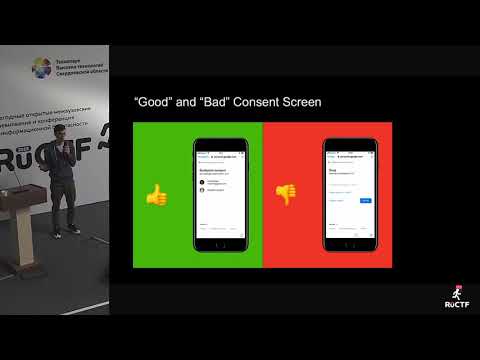
Уязвимости мобильного OAuth 2.0, Никита Ступин, Mail.ru. RuCTF 2019See more
Securing Your APIs with OAuth 2.0 - API DaysSee more

How Google is using OAuth - Part 3: Call Google OAuth Endpoint and Gmail APISee more
Vulnerabilities of mobile OAuth 2.0 by Nikita Stupin, Mail.ruSee more
